MGT 300 - CHAPTER 5
CHAPTER 5 👉 ORGANIZATIONAL STRUCTURES THAT SUPPORT STRATEGIC INITIATIVES
ORGANIZATIONAL STRUCTURES
⇝ Organizational employees must work closely together to develop strategic initiatives that create competitive advantages.
⇝ Ethics and security are two fundamental building blocks that organizations must base their businesses upon.
IT ROLES AND RESPONSIBILITIES
👀 Information technology is a relatively new functional area, having only been around formally for around 40years.
👀 Recent IT-related strategic positions :
👊 Chief Information Officer (CIO)
👊 Chief Technology Officer (CTO)
👊 Chief Security Officer (CSO)
👊 Chief Privacy Officer (CPO)
👊 Chief Knowledge Office (CKO)
Chief Information Officer (CIO)
👾 Oversees all uses of IT and ensures the strategic alignment of IT with business goals and objectives.
👾 Broad CIO functions include :
🙈 Manager - Ensuring the delivery of all IT projects, on time and within budget
🙈 Leader - Ensuring the strategic vision of IT is in line with the strategic vision of the organization
🙈 Communicator - Building and maintaining strong executive relationships
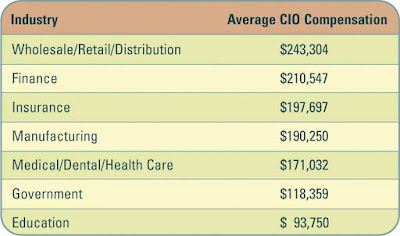
Average CIO compensation by industry

What concerns CIOs the most
Chief Technology Officer (CTO)
👾 Responsible for ensuring the throughput, speed, accuracy, availability and reliability of IT
Chief Security Officer (CSO)
👾 Responsible for ensuring the security of IT systems
Chief Privacy Officer (CPO)
👾 Responsible for ensuring the ethical and legal use of information
Chief Knowledge Office (CKO)
👾 Responsible for collecting, maintaining and distributing the organization's knowledge

Skills pivotal for success in executive IT roles
The Gap Between Business Personnel and IT Personnel
👯 Business personnel possess expertise in functional areas such as marketing, accounting, and sales
👯 IT personnel have the technological expertise
👯 This typically causes a communications gap between the business personnel and IT personnel
Improving Communications
🙊 Business personnel must seek to increase their understanding of IT
🙊 IT personnel must seek to increase their understanding of the business
🙊 Responsible of the CIO to ensure effective communication between business personnel and IT personnel
Organizational Fundamentals - Ethics and Security
🙌 Ethics and security are two fundamental building blocks that organizations must base their businesses on to be successful.
🙌 In recent years, such events as the Enron and Martha Stewart, along with 9/11 have shed new light on the meaning of ethics and security.
Ethics
💕 The principles and standards that guide our behavior toward other people
💕 Privacy is a major ethical issue
😁 Privacy ⇝ The right to be left alone when you want to be, to have control over your own personal possessions and not to be observed without your consent.
💕 Issues affected by technology advances
😁 Intellectual property ➢ Intangible creative work that is embodied in physical form
😁 Copyright ➢ The legal protection afforded an expression of an idea such as a song, video game and some types of proprietary documents.
😁 Fair use doctrine ➢ In certain situations, it is legal to use copyrighted material
😁 Pirated software ➢ The unauthorized use,duplication, distribution, or sale of copyrighted software
😁 Counterfeit software ➢ Software that is manufactured to look like the real thing and sold as such.
💕 One of the main ingredients in trust is privacy
💕 Primary reasons privacy issues lost trust for e-business

Security
👾 Organizational information is intellectual capital - it must be protected
👾 Information security ⇝ The protection of information from accidental or intentional misuse by persons inside or outside an organization.
👾 E-business automatically creates tremendous information security risks for organizations
THE END CHAPTER 5
ORGANIZATIONAL STRUCTURES
⇝ Organizational employees must work closely together to develop strategic initiatives that create competitive advantages.
⇝ Ethics and security are two fundamental building blocks that organizations must base their businesses upon.
IT ROLES AND RESPONSIBILITIES
👀 Information technology is a relatively new functional area, having only been around formally for around 40years.
👀 Recent IT-related strategic positions :
👊 Chief Information Officer (CIO)
👊 Chief Technology Officer (CTO)
👊 Chief Security Officer (CSO)
👊 Chief Privacy Officer (CPO)
👊 Chief Knowledge Office (CKO)
Chief Information Officer (CIO)
👾 Oversees all uses of IT and ensures the strategic alignment of IT with business goals and objectives.
👾 Broad CIO functions include :
🙈 Manager - Ensuring the delivery of all IT projects, on time and within budget
🙈 Leader - Ensuring the strategic vision of IT is in line with the strategic vision of the organization
🙈 Communicator - Building and maintaining strong executive relationships

Average CIO compensation by industry

What concerns CIOs the most
Chief Technology Officer (CTO)
👾 Responsible for ensuring the throughput, speed, accuracy, availability and reliability of IT
Chief Security Officer (CSO)
👾 Responsible for ensuring the security of IT systems
Chief Privacy Officer (CPO)
👾 Responsible for ensuring the ethical and legal use of information
Chief Knowledge Office (CKO)
👾 Responsible for collecting, maintaining and distributing the organization's knowledge

Skills pivotal for success in executive IT roles
The Gap Between Business Personnel and IT Personnel
👯 Business personnel possess expertise in functional areas such as marketing, accounting, and sales
👯 IT personnel have the technological expertise
👯 This typically causes a communications gap between the business personnel and IT personnel
Improving Communications
🙊 Business personnel must seek to increase their understanding of IT
🙊 IT personnel must seek to increase their understanding of the business
🙊 Responsible of the CIO to ensure effective communication between business personnel and IT personnel
Organizational Fundamentals - Ethics and Security
🙌 Ethics and security are two fundamental building blocks that organizations must base their businesses on to be successful.
🙌 In recent years, such events as the Enron and Martha Stewart, along with 9/11 have shed new light on the meaning of ethics and security.
Ethics
💕 The principles and standards that guide our behavior toward other people
💕 Privacy is a major ethical issue
😁 Privacy ⇝ The right to be left alone when you want to be, to have control over your own personal possessions and not to be observed without your consent.
💕 Issues affected by technology advances
😁 Intellectual property ➢ Intangible creative work that is embodied in physical form
😁 Copyright ➢ The legal protection afforded an expression of an idea such as a song, video game and some types of proprietary documents.
😁 Fair use doctrine ➢ In certain situations, it is legal to use copyrighted material
😁 Pirated software ➢ The unauthorized use,duplication, distribution, or sale of copyrighted software
😁 Counterfeit software ➢ Software that is manufactured to look like the real thing and sold as such.
💕 One of the main ingredients in trust is privacy
💕 Primary reasons privacy issues lost trust for e-business

Security
👾 Organizational information is intellectual capital - it must be protected
👾 Information security ⇝ The protection of information from accidental or intentional misuse by persons inside or outside an organization.
👾 E-business automatically creates tremendous information security risks for organizations
THE END CHAPTER 5

Comments
Post a Comment